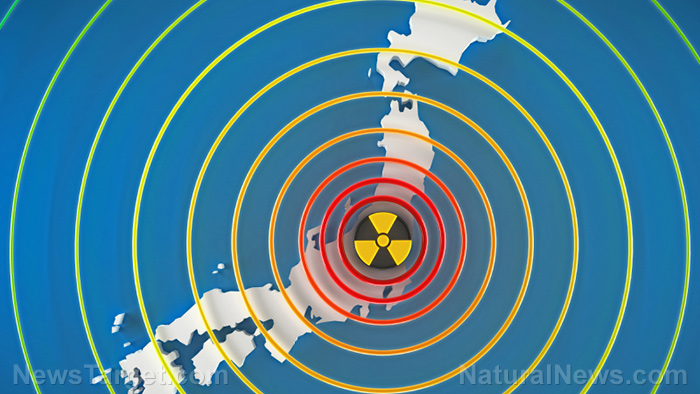
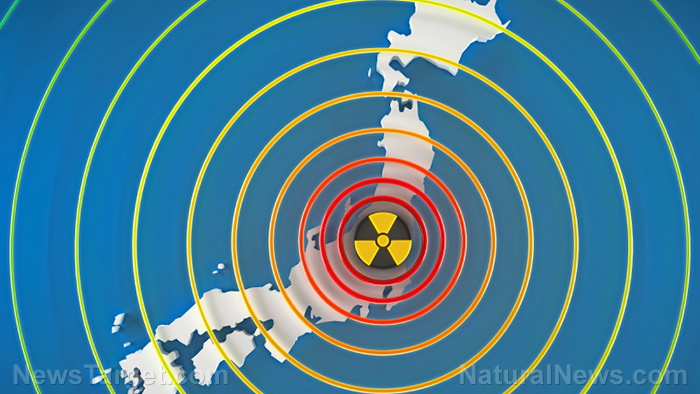
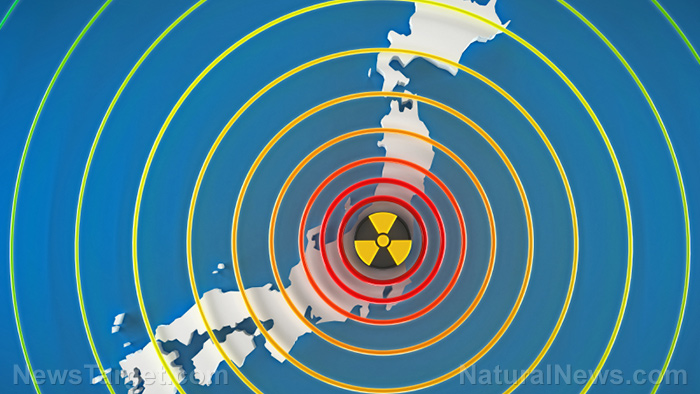
Nuclear power plants vulnerable to cyberattacks across the globe
10/09/2015 / By Greg White

Nuclear power plants have always carried their fair share of risks. A risk that has been widely ignored by the nuclear industry is the threat of cyberattacks. This sentiment rang true with respect to a new Chatham House report, which found most countries with civil nuclear infrastructure are vulnerable to cyberattacks.
The risk of cyberattacks is increasing as nuclear facilities become more reliant on digital systems and increasingly use commercial ‘off-the-shelf’ software. The report claims that cyber criminals could use this technology to trigger a nuclear catastrophe on par with the Fukushima disaster.
In 2011, an earthquake launched a tsunami that crippled three nuclear reactors at the Fukushima Daiichi site. Since the debacle, hundreds of tons of radioactive waste have polluted the environment and caused neighboring cities to become ghost towns. The meltdown claimed the lives of roughly 16,000 people and has been considered the worst nuclear disaster since the Chernobyl catastrophe in 1986.[1]
The Fukushima disaster was a product of poor decision making and the forces of nature. In particular, the Tokyo Electric Power Company (TEPCO), the company in charge of the power plant, underestimated the threat that tsunamis posed to the region when designing the facility. By ignoring the threat that cyberattacks pose to nuclear facilities, power plant administrators are guilty of the same negligence as the folks at TEPCO.
Weak security passwords and a failure to communicate
The report was published by the think tank Chatham House. Researchers looked at the cybersecurity of power plants spread across the globe for a period of 18 months. They conducted 30 interviews with government officials and senior nuclear officials in Canada, France, Germany, Japan, the UK, Ukraine and the US.[1]
The results of the study were sobering. In particular, the report found that nuclear power plants sprinkled across the globe were lacking in a number of basic security protocols. For example, weak passwords vulnerable to hacking, like “1234,” were used on a wide range of computer systems that control critical systems in power plants.
“Cyber security is still new to many in the nuclear industry,” Caroline Baylon, an author of the study, told the Financial Times. “They are really good at safety and, after 9/11, they’ve got really good at physical security. But they have barely grappled with cyber.”[1]
The researchers also found that many engineers bring their personal computers into work to manage facility systems. In addition, digital back doors are becoming increasingly common as companies use more monitoring systems.
A myth squandered
The report also squandered a prevalent myth that computer systems at nuclear facilities are invulnerable to hacking because they are disconnected from the public internet. To the contrary: The gap between the public internet and nuclear systems can easily be bridged with nothing but a hard drive, according to the report.
“Many people said it was simply not possible to cause a major incident like a release of ionising radiation with a cyber attack,” said Baylon, “but that’s not necessarily true.”[1]
Authors of the study concluded that a lack of communication between engineers and security personnel, coupled with insufficient training, were the reasons why so many power plants were susceptible to cyberattacks.
“This suggests the industry’s risk assessment may be inadequate; as a consequence, there is often insufficient spending on cyber security.”[1]
To help mitigate these risks, the researchers recommended the nuclear industry to develop guidelines to measure cybersecurity threats, start a dialogue between engineers and contractors, and adopt universal regulatory standards.[2]
Sources include:
(1) DailyMail.co.uk
(2) ChathamHouse.org
Submit a correction >>
Tagged Under:
cyberattacks, cybersecurity, hacking, nuclear power plants, radiation
This article may contain statements that reflect the opinion of the author
RECENT NEWS & ARTICLES
COPYRIGHT © 2017 FUKUSHIMAWATCH.COM
All content posted on this site is protected under Free Speech. FukushimaWatch.com is not responsible for content written by contributing authors. The information on this site is provided for educational and entertainment purposes only. It is not intended as a substitute for professional advice of any kind. FukushimaWatch.com assumes no responsibility for the use or misuse of this material. All trademarks, registered trademarks and service marks mentioned on this site are the property of their respective owners.